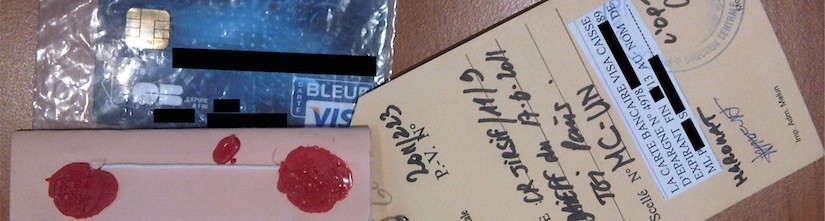In late 2009, my colleagues and I discovered a serious vulnerability in EMV, the most widely used standard for smart card payments, known as “Chip and PIN” in the UK. We showed that it was possible for criminals to use a stolen credit or debit card without knowing the PIN, by tricking the terminal into thinking that any PIN is correct. We gave the banking industry advance notice of our discovery in early December 2009, to give them time to fix the problem before we published our research. After this period expired (two months, in this case) we published our paper as well explaining our results to the public on BBC Newsnight. We demonstrated that this vulnerability was real using a proof-of-concept system built from equipment we had available (off-the shelf laptop and card reader, FPGA development board, and hand-made card emulator).
After the programme aired, the response from the banking industry dismissed the possibility that the vulnerability would be successfully exploited by criminals. The banking trade body, the UK Cards Association, said:
“We believe that this complicated method will never present a real threat to our customers’ cards. … Neither the banking industry nor the police have any evidence of criminals having the capability to deploy such sophisticated attacks.”
Similarly, EMVCo, who develop the EMV standards said:
“It is EMVCo’s view that when the full payment process is taken into account, suitable countermeasures to the attack described in the recent Cambridge Report are already available.”
It was therefore interesting to see that in May 2011, criminals were caught having stolen cards in France then exploiting a variant of this vulnerability to buy over €500,000 worth of goods in Belgium (which were then re-sold). At the time, not many details were available, but it seemed that the techniques the criminals used were much more sophisticated than our proof-of-concept demonstration.
We now know more about what actually happened, as well as the banks’ response, thanks to a paper by the researchers who performed the forensic analysis that formed part of the criminal investigation of this case. It shows just how sophisticated criminals could be, given sufficient motivation, contrary to the expectations in the original banking industry response.
While our equipment fitted into a backpack, and the Smart Card Detective could be hidden up a sleeve, the criminals wrote the software which exploited the vulnerability onto a programmable smart card popular with hobbyists (the Atmel-based FUN card), then carefully connected it to the chip taken from a stolen payment card. This package was then put into another payment card, replacing the genuine chip, whilst still being thin enough (0.8mm) to fit into a payment card terminal’s slot!
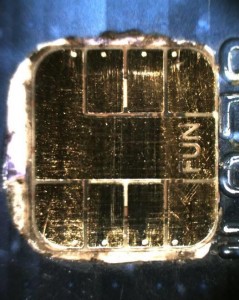
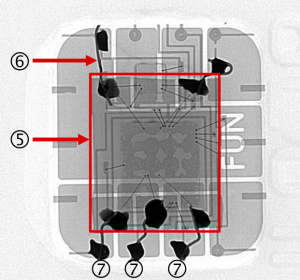
The criminals’ software didn’t just trick the terminal into accepting any PIN, but also pretended that the card had done fewer transactions than it really had — by locking the Application Transaction Counter (ATC) to a fixed number. This was to prevent the terminal from going online and checking the transaction with the bank, and so allowing the fraudulent card to be used even once the cardholder had reported the genuine one as stolen. This possibility was not something that we discussed in our paper, or even had implemented (it wouldn’t have worked in the UK because almost all transactions are checked with the bank here, unlike in France or Belgium).
The new paper poses an interesting question. To what extent, if any, did the criminals make use of our research? There’s no strong evidence in either direction. On one hand, the timing makes the scenario of the criminals learning from our paper plausible: our paper was published in February 2010 and the criminals were caught in May 2011 — this period of time is more than sufficient to perfect the techniques seen, especially since French criminals have been developing fraudulent EMV smart cards since at least 2001.
On the other hand, the criminals could have come up with the techniques partially or fully independently from us. Supporting this hypothesis is the fact that both the criminals’ hardware engineering and the fraud techniques are considerably more sophisticated than our own. We had not even considered the possibility of tampering with the ATC to force the terminal to stay offline. The UK Cards Association also claimed that the vulnerability was known of in the industry already, so perhaps criminals knew too. Finally, we heard privately that our research caused banks to start searching for the forensic signature of the vulnerability being exploited. So perhaps the reason for the timing is that criminals were already using this technique to commit fraud and our disclosure caused them to be discovered.
What we do know with confidence is that had the banks acted to close the vulnerability immediately after we notified them, these criminals would not have been able to commit this fraud. The authors of the new paper developed, tested and deployed two ways to defeat the fraudulent cards within a week. These changes were not widespread in the UK though, as they would also have prevented our equipment from working, and we’ve never encountered any problems doing demonstrations. I hope the banking industry will learn from this lesson when dealing with future vulnerabilities that are disclosed to them — criminals will be as sophisticated as they need to be.